Delegated Authentication for Veeva CRM
- iPad
- iPhone
Veeva CRM supports delegated authentication, or single sign-on (SSO), allowing users to sign into Veeva CRM with third-party credentials. Customers must set up a delegated authentication endpoint with their identity provider (IDP; for example, Okta or PingFederate).
To configure delegated authentication in Salesforce:
- Navigate to the Single Sign-On Settings.
- Select Edit.
- Select Disable login with Salesforce credentials.
- Select Save.
- Select Edit.
- Enter the URL of the IDP’s delegated authentication endpoint in the Delegated Gateway URL field.
- Select Save.
- Navigate to the appropriate end user profiles.
- Select Edit.
- Select the Is Single Sign-On Enabled check box in the Administrative Permissions.
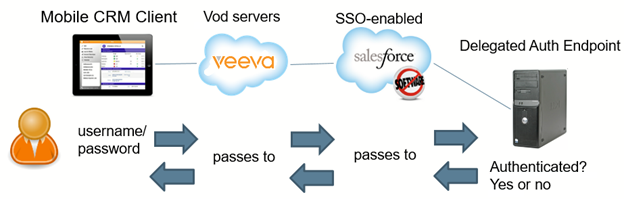
In this diagram, the flow of information begins with the user entering a username and password on the offline device (iPad or Windows) Those credentials are then sent to the Identity Provider ,who then returns the Salesforce username and token. This is sent to the Vod server and then to SFDC. When SFDC recognizes the user is SSO-enabled, they forward the credentials to the Delegated Authentication Endpoint. Delegated Authentication Endpoint authenticates the credentials and responds either yes or no. Depending on the response, the offline device receives the response and either logs in the user or gives an error.
Using Token Authentication
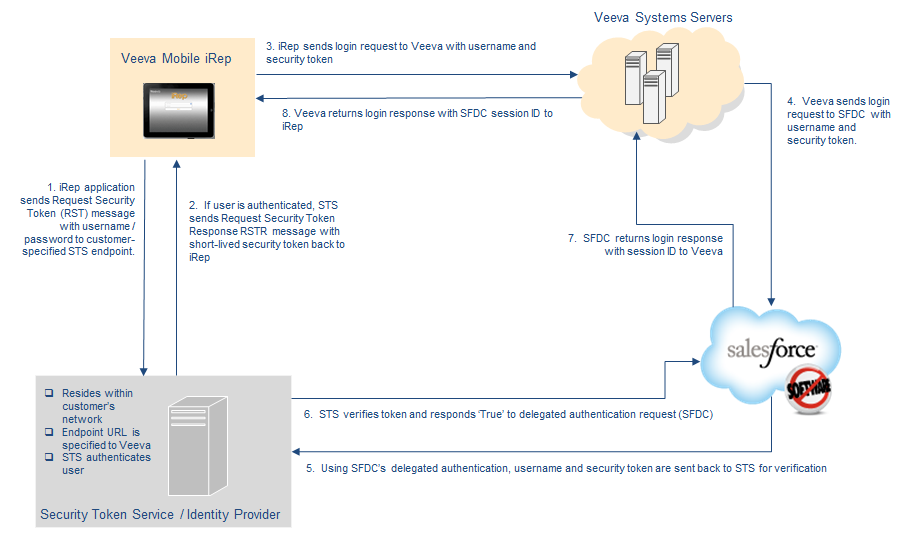
To provide greater security, customers can implement a security token service (STS) in addition to delegated authentication. Implementing an STS ensures passwords are only sent to endpoints controlled by the customer.
If an STS is implemented, when a user signs into the Veeva CRM app, their username and password are first sent to the customer-hosted STS, which returns a token to Veeva CRM. Veeva CRM then uses the username and token to verify the signin with Salesforce and the delegated authentication endpoint. Customers must set up the endpoint to authenticate a username and token instead of a username and password.
The authentication exchange between the Veeva CRM app and a customer’s STS is based on SOAP web services and the WS-Trust standard. The Veeva CRM sends a request security token (RST) message to the STS and receives a request security token response (RSTR) message back. The security token is then extracted from the response message and passed to Salesforce for verification.
Documentation for WS-Trust is found on the OASIS open standards website (https://www.oasis-open.org/standards/#wstrustv1.3) and includes:
- the WSDL document (http://docs.oasis-open.org/ws-sx/ws-trust/200512/ws-trust-1.3.wsdl) and
- the XML schema (http://docs.oasis-open.org/ws-sx/ws-trust/200512/ws-trust-1.3.xsd)
The exchange of information is shown in the following diagram:
To enable delegated authentication with STS for Veeva CRM for iPad in your org:
- Implement a security token service (STS) that can receive request security token (RST) messages and return request security token response (RSTR) messages based on WS-Trust.
- Ensure Salesforce delegated authentication is enabled for your org.
-
Configure the MDM with the endpoint URL for the RST and RSTR messages and the Delegated Gateway URL configured in Salesforce. Both URLs must be accessible via the internet. See Delegated Authentication for Veeva CRM via MDM for more information.
The following is an example RST Veeva CRM sends to the STS at the endpoint URL specified by the customer:
<?xml version="1.0"?>
<soapenv:Envelope xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/">
<soapenv:Header>
<wsse:Security xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd" soapenv:mustUnderstand="1">
<wsu:Timestamp xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
<wsu:Created>2012-02-17T09:37:28.098Z</wsu:Created>
<wsu:Expires>2012-02-17T19:37:28.098Z</wsu:Expires>
</wsu:Timestamp>
<wsse:UsernameToken xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd" wsu:Id="usernameToken">
<wsse:Username>salesforce_username@customer.org</wsse:Username>
<wsse:Password Type="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#PasswordText">corp_directory_password</wsse:Password>
</wsse:UsernameToken>
</wsse:Security>
<wsa:Action xmlns:wsa="http://www.w3.org/2005/08/addressing" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">http://docs.oasis-open.org/ws-sx/ws-trust/200512/Issue</wsa:Action>
</soapenv:Header>
<soapenv:Body xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
<wst:RequestSecurityToken xmlns:wst="http://docs.oasis-open.org/ws-sx/ws-trust/200512/">
<wst:TokenType/>
<wst:RequestType>http://docs.oasis-open.org/ws-sx/ws-trust/200512/Issue</wst:RequestType>
<wsp:AppliesTo xmlns:wsp="http://schemas.xmlsoap.org/ws/2004/09/policy">
<wsa:EndpointReference xmlns:wsa="http://www.w3.org/2005/08/addressing">
<wsa:Address>http_endpoint_url_for_step_5</wsa:Address>
</wsa:EndpointReference>
</wsp:AppliesTo>
<wst:Claims/>
<wst:OnBehalfOf>
<wsse:SecurityTokenReference xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<wsse:Reference URI="usernameToken" ValueType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-username-token-profile-1.0#UsernameToken"/>
</wsse:SecurityTokenReference>
</wst:OnBehalfOf>
</wst:RequestSecurityToken>
</soapenv:Body>
</soapenv:Envelope>
The following is an example RSTR Veeva CRM expects back from the STS. The entire security token is extracted from the message, base64 encoded, and sent to Salesforce in the signin request sent by CRM.
<S11:Envelope xmlns:S11="http://schemas.xmlsoap.org/soap/envelope/">
<S11:Header>
<add:To xmlns:add="http://www.w3.org/2005/08/addressing">
http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anonymous</add:To>
<add:Action xmlns:add="http://www.w3.org/2005/08/addressing">
http://docs.oasis-open.org/ws-sx/ws-trust/200512/RSTRC/IssueFinal</add:Action>
<wsse:Security S11:mustUnderstand="1" xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<wsu:Timestamp wsu:Id="4ad9d92b-dd36-4ae7-a372-a82ee0d4b213" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
<wsu:Created>2012-02-17T09:38:04.233Z</wsu:Created>
<wsu:Expires>2012-02-17T09:48:04.233Z</wsu:Expires>
</wsu:Timestamp>
</wsse:Security>
</S11:Header>
<S11:Body>
<ns:RequestSecurityTokenResponseCollection xmlns:ns="http://docs.oasis-open.org/ws-sx/ws-trust/200512/">
<ns:RequestSecurityTokenResponse>
<ns:TokenType>http://docs.oasis-open.org/wss/oasis-wss-saml-token-profile-1.1#SAMLV2.0</ns:TokenType>
<ns:RequestedSecurityToken>
<saml:Assertion ID="_mdqaUZ4BWj_672ve1bznz6Vu.t" IssueInstant="2012-09-17T09:38:04.108Z" Version="2.0" xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">
<saml:Issuer>sts_idp_issuer_url</saml:Issuer>
<ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:SignedInfo>
<ds:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/>
<ds:SignatureMethod Algorithm="http://www.w3.org/2000/09/xmldsig#rsa-sha1"/>
<ds:Reference URI="#_mdqaUZ4BWj_672ve1bznz6Vu.t">
<ds:Transforms>
<ds:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature"/>
<ds:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/>
</ds:Transforms>
<ds:DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha1"/>
<ds:DigestValue>SJK1qp6tIv9CRPZ8Twsx248RRQw=</ds:DigestValue>
</ds:Reference>
</ds:SignedInfo>
<ds:SignatureValue>
a7j8uANkQeDBMnDXmCCqW7x19xx1GOhB19aJ+GxCAQXiJunF9a23fcBCBRmPLwu6B5Q5NUtJiFZe
EjKIQqulTpVJ14UbuP4Q0GJiUOjgPzCvxMgnDuIB9W2kSdejQWVs9xqtLXYGjEoyo2dY7XDZpfvQ
LspTvBjkdM41ScSydEg=
</ds:SignatureValue>
<ds:KeyInfo>
<wsse:SecurityTokenReference xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<wsse:KeyIdentifier ValueType="http://docs.oasis-open.org/wss/oasis-wss-soap-message-security-1.1#ThumbprintSHA1">7G/+BJtRSRRfmmo3JfbuDx+f+TY=</wsse:KeyIdentifier>
</wsse:SecurityTokenReference>
</ds:KeyInfo>
</ds:Signature>
<saml:Subject>
<saml:NameID Format="urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified">salesforce_username@customer.org</saml:NameID>
<saml:SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer"/>
</saml:Subject>
<saml:Conditions NotBefore="2012-02-17T22:43:04.233Z" NotOnOrAfter="2012-02-17T22:53:04.233Z">
<saml:AudienceRestriction>
<saml:Audience>sts_idp_issuer_url</saml:Audience>
</saml:AudienceRestriction>
</saml:Conditions>
<saml:AuthnStatement AuthnInstant="2012-02-17T22:48:04.108Z" SessionIndex="_mdqaUZ4BWj_672ve1bznz6Vu.t">
<saml:AuthnContext>
<saml:AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:unspecified</saml:AuthnContextClassRef>
</saml:AuthnContext>
</saml:AuthnStatement>
</saml:Assertion>
</ns:RequestedSecurityToken>
<ns:Lifetime>
<wsu:Created xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">2012-08-15T22:48:04.108Z</wsu:Created>
<wsu:Expires xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">2012-08-15T23:18:04.108Z</wsu:Expires>
</ns:Lifetime>
<ns:RequestedAttachedReference>
<wsse:SecurityTokenReference wsse11:TokenType="http://docs.oasis-open.org/wss/oasis-wss-saml-token-profile-1.1#SAMLV2.0" xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd" xmlns:wsse11="http://docs.oasis-open.org/wss/oasis-wss-wssecurity-secext-1.1.xsd">
<wsse:KeyIdentifier ValueType="http://docs.oasis-open.org/wss/oasis-wss-saml-token-profile-1.1#SAMLID">_mdqaUZ4BWj_672ve1bznz6Vu.t</wsse:KeyIdentifier>
</wsse:SecurityTokenReference>
</ns:RequestedAttachedReference>
</ns:RequestSecurityTokenResponse>
</ns:RequestSecurityTokenResponseCollection>
</S11:Body>
</S11:Envelope>